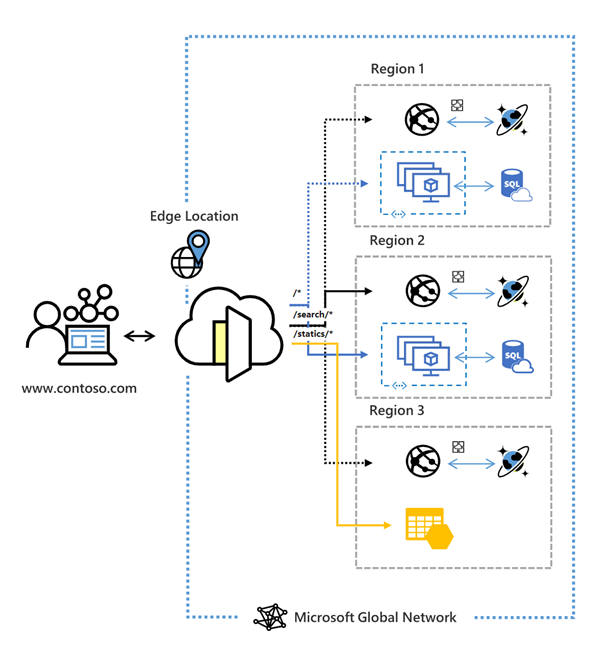
10 Steps to get started with Azure for partners. #9
#9 Storing data in Azure
By Christopher Melendez
Introduction to Azure Storage – Cloud storage on Azure | Microsoft Docs
There are different types of data, and it comes in all shapes and sizes. There is no one solution that fits these variations. For that reason, we need to understand the requirements, and classify our data first, to choose the best storage solution. The main things to focus on would be how to classify your data, how will this data be used in your environment, and what technology will give you the best performance for your applications and end users.
Azure SQL fundamentals – Learn | Microsoft Docs
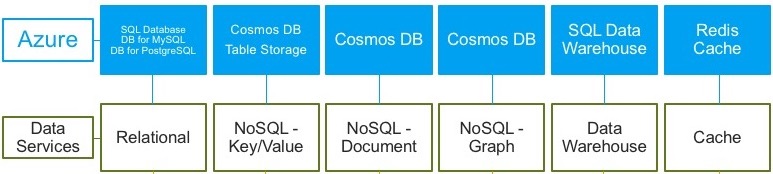
Structured data, often called relational data, is data that you know should never change its schema. For example, a customer database or employee database. You know what the important information is, and it’s unlikely that this will change. Most of the time, structured data is stored in a database with tables with rows and columns. There’s always a key column as well, this indicates how one row relates to data in another row. Once the data is in the database in this format, you can use a language like SQL to parse it. Relational data or structed data in Azure should be stored in an Azure SQL Database, SQL Managed Instance, or SQL Server on a Virtual Machine.
Work with NoSQL data in Azure Cosmos DB learning path – Learn | Microsoft Docs
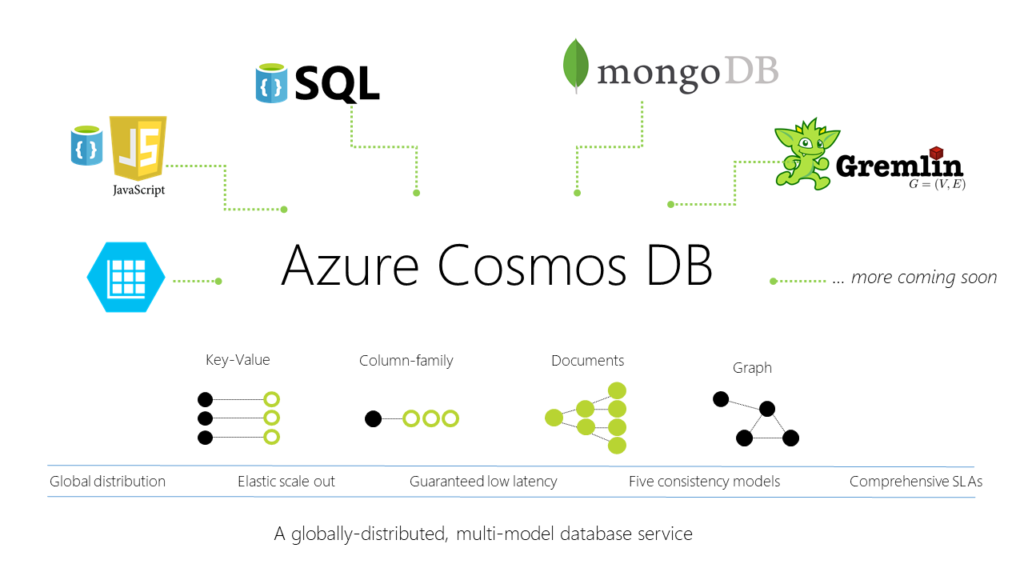
Semi-structed data is not as organized as structured data. This dataset can change very often, which would not fit into tables, rows, and columns very well. Semi-structured data is often called non-relational data and should be stored in a NoSQL database. Azure’s NoSQL database is called Cosmos DB. This technology is perfect for databases that house online stores with products that often change.
Store and share files in your app with Azure Files – Learn | Microsoft Docs
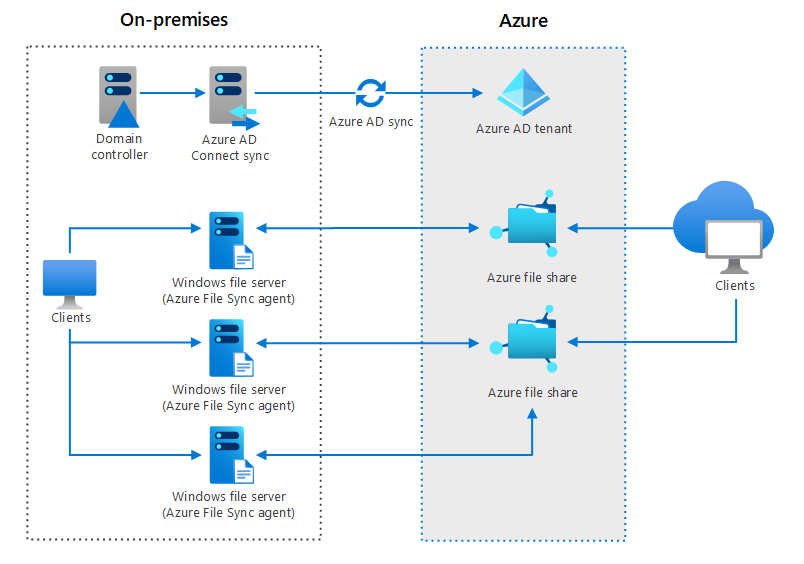
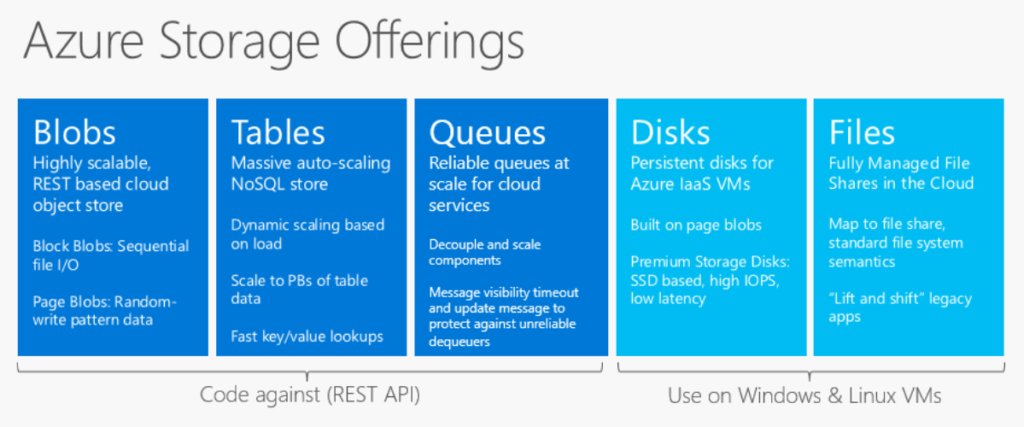
Unstructured data is best known to be data that lives on a traditional file server. Data types like office files, word documents, and even media files such as photos, videos, and audio files. This data is best stored in Azure blob, on an SMB share called Azure Files. It’s a simple, secure, and serverless cloud file share that provides the mechanism to extend your on-premises file servers into Azure.
Choose the right disk storage for your virtual machine workload
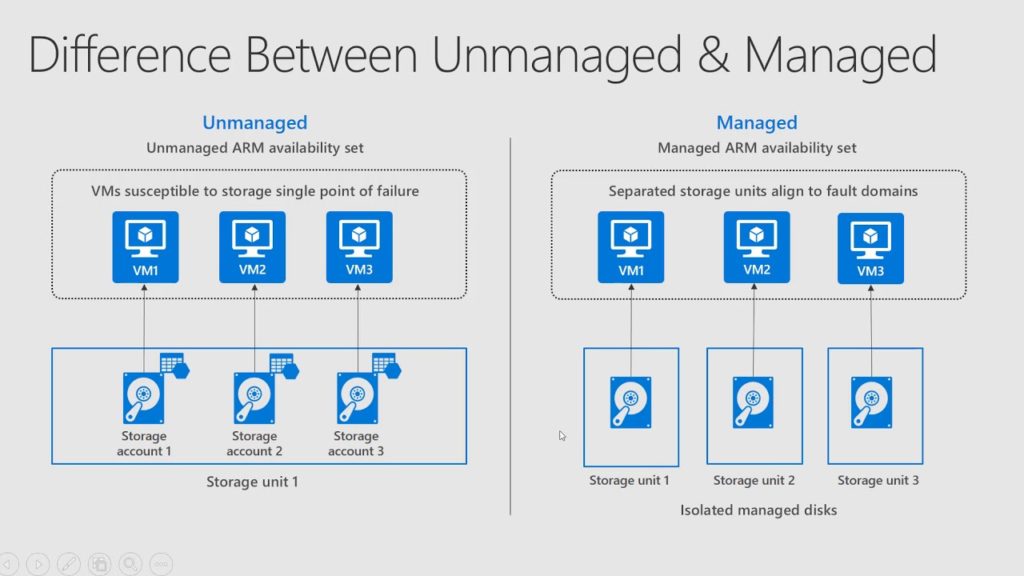
The fourth type of data we should think about is Virtual Machines in Azure. We need understand what storage options we should go with. Selecting the appropriate storage for your Virtual Machine is also part of the VM deployment process and should be planned on ahead of time. Should you go with Premium SSD or Standard HDD to save costs? Are we going with managed or unmanaged disks? Should we leverage SAS keys or attach storage to a Virtual Machine and present as a share? There are so many options for us in Azure, that’s what makes it great, but it also makes it complicated.
Store data in Azure learning path – Learn | Microsoft Docs
Managed Disks will probably be the disk that you use most often in Azure. It’s a virtual disk like unmanaged disks, the big difference is that Azure manages all the required physical infrastructure for us. Unmanaged disk does not have this feature, so deploying them in your environment can take a lot more planning and consideration. Some other benefits of managed disks include integration with availability sets and zones, support for Azure Backup, and support for encryption. Unmanaged disks, like managed disks, are stored as page blobs in an Azure Storage account. The big difference is maintaining this storage account manually, this includes keeping track of IOPS limits within the storage account, to make sure there are no performance issues or overprovisioning.
Architect storage infrastructure in Azure learning path – Learn | Microsoft Docs
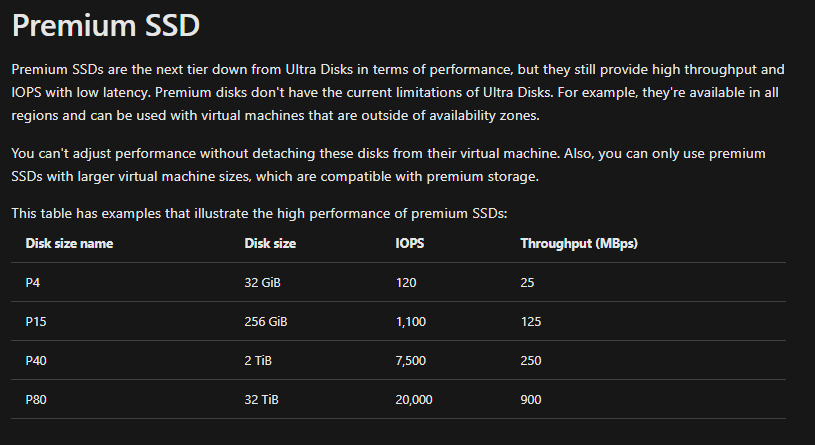
There are a few disk types that we get to choose from in Azure, and they all provide different performance. Ultra SSD disks provide the highest disk performance available in Azure, and with that, are the most expensive. This storage type should be chosen when the application is very demanding and needs high IOPS, high throughput, and low latency. Ultra disks are the newest addition to disk types, so they are currently only available in a subset of Azure regions. Premium SSD is the next disk type on the list, they are a tier down from Ultra in performance, but will probably be your option for high throughput and IOPS with low latency. They are considered the go to for Production workloads that have high demand, such as SQL Server data disks. Not all the virtual machines support premium disks however, they are compatible with larger virtual machine sizes. For that reason, Standard SSD will probably be the disk type for most of your production workloads. Virtual disks can be migrated to premium SSD at any time if customers find that their performance is just not good enough. Standard SSD disks in Azure are more cost-effective compared to Premium SSD, for virtual machines that need consistent performance at lower speeds. They are available to attach to any virtual machine size, which makes them the most common option.